DDoS IRC Bot Malware Spreading Through Korean WebHard Platforms
An IRC (Internet Relay Chat) bot strain programmed in GoLang is being used to launch distributed denial-of-service (DDoS) attacks targeting users in Korea.
“The malware is being distributed under the guise of adult games,” researchers from AhnLab’s Security Emergency-response Center (ASEC) said in a new report published on Wednesday. “Additionally, the DDoS malware was installed via downloader and UDP RAT was used.”
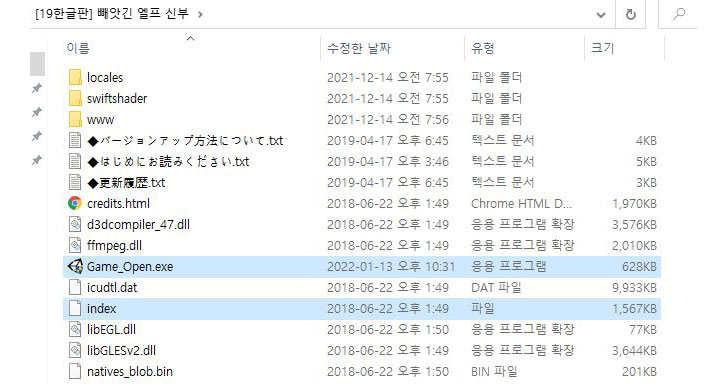
The attack works by uploading the malware-laced games to webhards, which refers to a web hard drive or a remote file hosting service, in the form of compressed ZIP archives that, when opened, includes an executable (“Game_Open.exe”) that’s orchestrated to run a malware payload aside from launching the actual game.
This payload, a GoLang-based downloader, establishes connections with a remote command-and-control (C&C) server to retrieve additional malware, including an IRC bot that can perform DDoS attacks.
“It is also a type of DDoS Bot malware, but it uses IRC protocols to communicate with the C&C server,” the researchers detailed. “Unlike UDP Rat that only supported UDP Flooding attacks, it can also support attacks such as Slowloris, Goldeneye, and Hulk DDoS.”
GoLang’s low development difficulties and its cross-platform support have made the programming language a popular choice for threat actors, the researchers added.
“The malware is being distributed actively via file sharing websites such as Korean webhards,” AhnLab said. “As such, caution is advised when approaching executables downloaded from a file-sharing website. It is recommend[ed] for the users to download products from the official websites of developers.”
[ad_2]
Share this news on your Fb,Twitter and Whatsapp
Times News Network:Latest News Headlines
Times News Network||Health||